The modern community is developing rapidly. One of the branches for the development of the future is IoT or else as it is intended to call - the Internet of things. This is a very useful opportunity for the community to facilitate the performance of some important functions. However, IoT is also vulnerable to hacker attacks. But it is worth noting that many projects are already concerned about this problem. One such project is NOVAM.
The NOVAM project is designed to monitor, detect and neutralize threats to the IoT network. In addition, an additional feature of NOVAM is that the project features audit, verification, and ongoing monitoring of threats.
NOVAM was created in the image and likeness of the human immune system. Its main advantages are adaptation and self-healing. To these two benefits, the creators of NOVAM have added another interesting feature - machine learning. This will give NOVAM the opportunity to adapt to the modern realities of hacking art.

Device protection

As you know, the main component of IoT are the devices and applications that control them. Hackers can take advantage of this, and even penetrate our home. What needs to be done to rid yourself of this possibility? First, make connecting to other devices safe. Secondly, constantly monitor the software on other devices and look for possible vulnerabilities. With these two points copes NOVAM. He is the one who will be able to ensure stable and safe operation of devices and applications, and constantly check the installed applications for vulnerabilities.
Network security

We know that individual devices can be connected to the network, as well as nodes in large enterprises. The more devices in one node, the easier it is to attack and it is more difficult to calculate the possible vulnerability. NOVAM created a functional that stands at the beginning of the node, so to speak at the connection point and checks all possible connections to this node. Autonomous monitoring, identification and instant response to threats are the main features of NOVAM.
Confidentiality

Despite the fact that the NOVAM system is fully embedded in devices and networks, all information remains inside the network and is not submitted for universal consideration. Protecting equipment, identifying threats with complete confidentiality - these are the main features of NOVAM.
Globality

If you think that NOVAM is only the protection of individual devices and networks, this is not so. NOVAM can monitor for the presence of vulnerabilities simultaneously multiple chains and nodes. This compares, monitors, identifies and identifies threats. Next, there is a choice of action. Depending on the possibility of the threat, NOVAM can automatically remove or clear the problem, mitigate, replace or quarantine it.

IoT monitoring

Own technology NOVAM allows you to constantly monitor the operation of IoT-devices, monitor them for vulnerabilities at any time.
Check

Own technology allows you to check the performance of devices and applications, search and fix vulnerabilities. At the same time, it is possible to check for application compromising, the possibility of changing their component through a vulnerability. The conclusion is simple: NOVAM is a whole system that prevents the introduction of vulnerabilities into the network. NOVAM provides everyone with a full package of services.
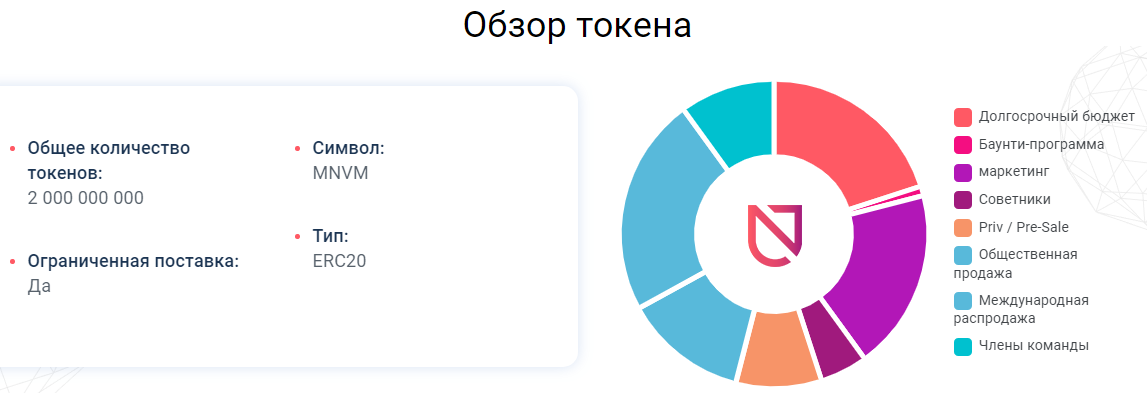
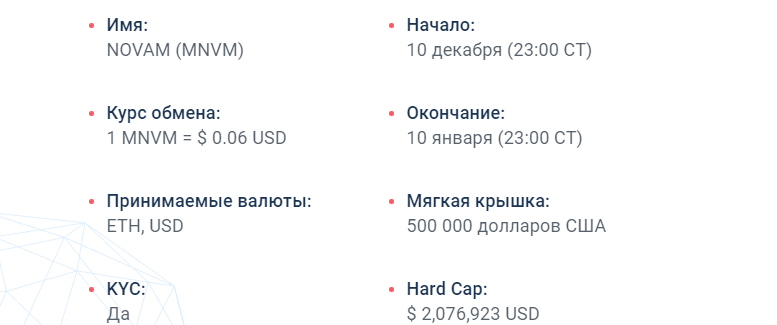
TOKEN:
NOVAM's own issued token is a license for performance. Token promotes license verification, authentication, and other issues.
ROADMAP:
3 square meters 2017 - development of the project idea;
Market research.
4 square meters 2017 - IoT manufacturers market research.
Q1 2018 - continued market research;
Creating project documentation.
2 square meters 2018 - holding consultations;
Preparing for a marketing campaign.
3 square meters 2018 - preparation for the sale of tokens.
4 square meters 2018 - creating a project team;
Check system performance.
Q1 2019 - testing the system by individuals;
Conclusion of the first partnership agreements.
2 square meters 2019 - development of the AI network;
Test Network TestNET.
3 square meters 2019 - API development;
Analytics based on Google Analytics.
4 square meters 2019 - Analytics testing;
API testing using NOVAM TestNET.
Q1 2020 - TestNET beta release.
2 square meters 2020 - access to new markets.
3 square meters 2020 - release of AI-products.
4 square meters 2020 - attracting partners and customers.
FOR MORE INFORMATION VISIT THE LINK BELOW:
AUTHOR:rizalkurniawan58
ETH:0x7F983c8659F5Ed19011F5Be67dCd8F9644b2097A

Tidak ada komentar:
Posting Komentar